Building Expertise Through Hands-On Practice
Codio’s Cryptographic Principles and Applications course materials are designed to provide learners with immersive, hands-on experiences that bridge the gap between theory and real-world application.
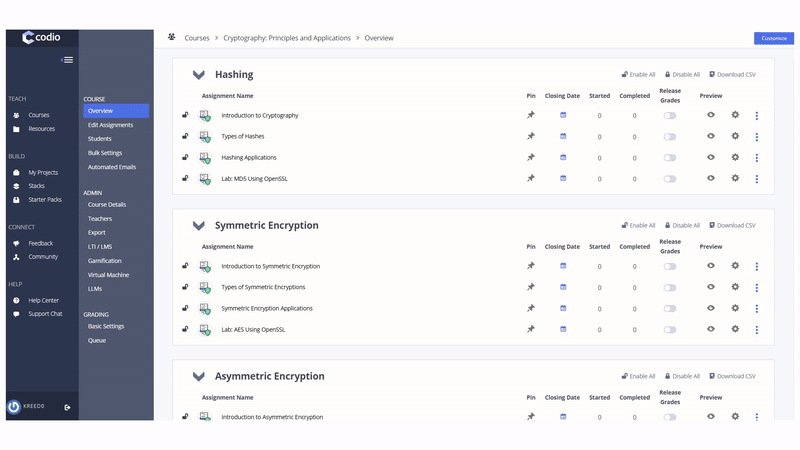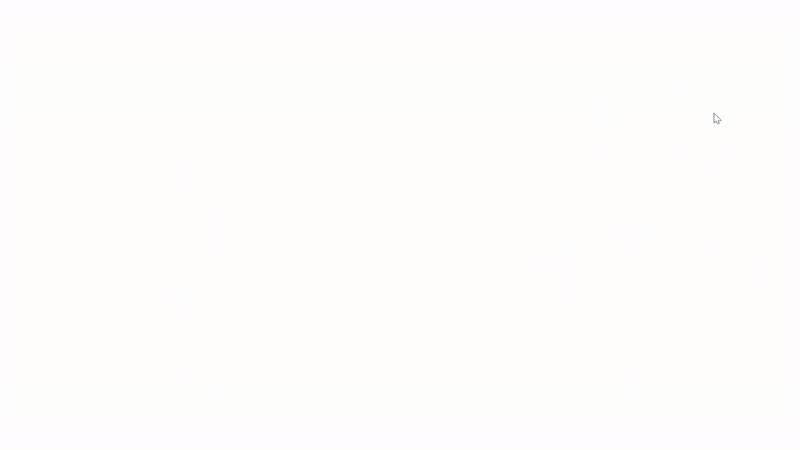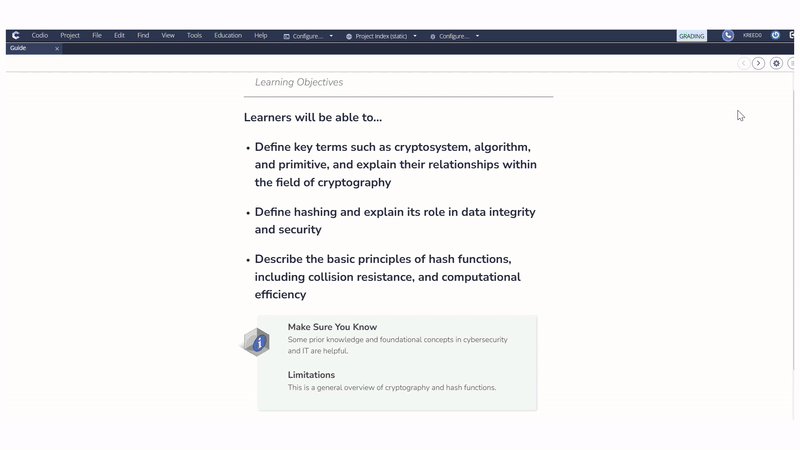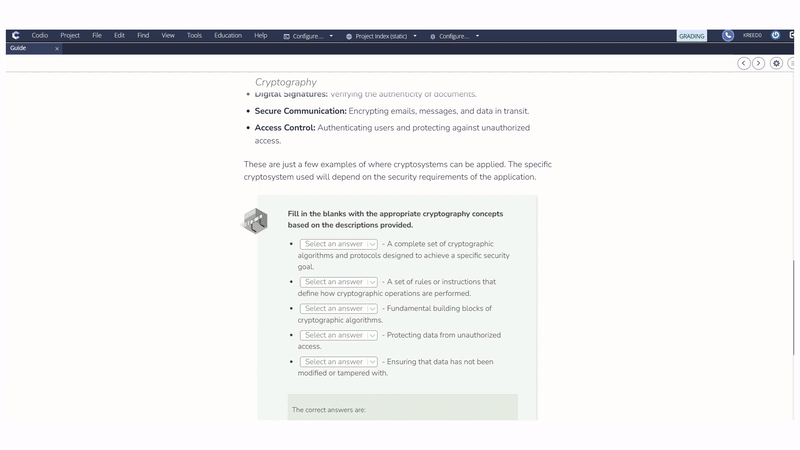
Encouraging Customizating Through Modularity
Codio’s Cryptography content isn’t a rigid, one-size-fits-all solution. The curriculum is structured in a modular format, with natural break points where instructors can adapt the material to best suit their teaching objectives. Whether reordering topics, renaming units, or adding custom content, instructors can easily tailor the learning experience. Codio’s flexible authoring tools also allow instructors to create their own content, ensuring that the course meets the specific needs of their students while maintaining a strong focus on the fundamentals of cryptography.