This course requires the use of (VMs) Virtual Machines which are an additional cost. To enable this for your organization, send an email to help@codio.com with approximate details of the number of students who will require access to computed VMs.
Building Expertise Through Hands-On Practice
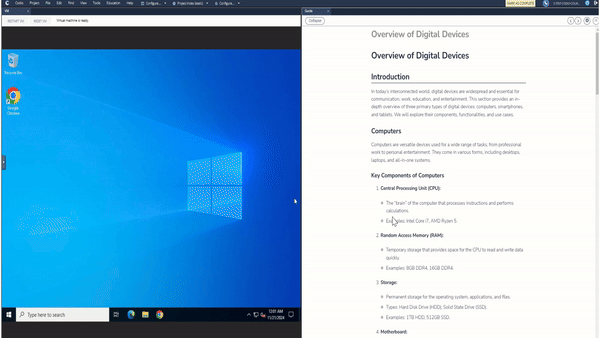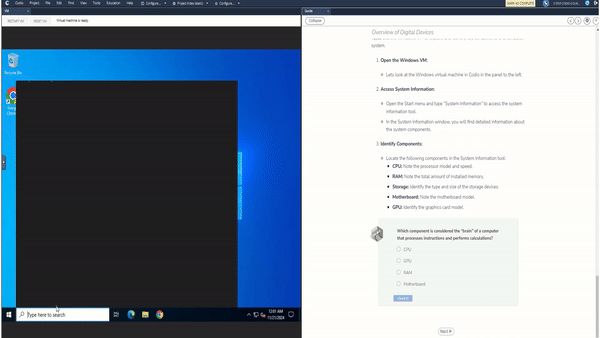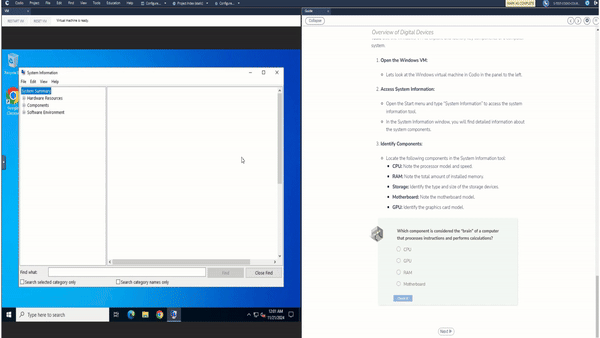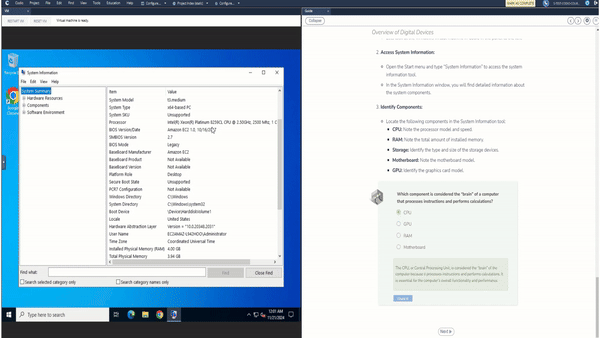
Codio’s Security Operations and Incident Response content is designed to immerse students in real-world security challenges, using Virtual Machines (VMs) to simulate secure and compromised environments. This allows learners to engage directly with tools and techniques in a controlled, practical setting. Each module is paired with interactive code editors and VMs to help students see the direct impact of their actions and solutions. With a hands-on, investigative approach, learners can experiment, troubleshoot, and understand cybersecurity in a deeply applied context.
Auto-Graded Assessments
We believe in the value of active feedback, which is why students receive immediate, rich feedback. In addition to feedback on the validity of a specific answer, students will also be provided with an explanation that includes the complete solution, as well as the steps that reached that destination. There are a wide variety of questions — all of which are auto-graded, giving students a sense of their understanding of the material right after they are introduced to it and as they attempt harder and harder problems.
Lowering the Barrier to Entry
Codio’s Cybersecurity curriculum is designed to meet students where they are, providing an accessible entry point to the world of security. We understand that cybersecurity, like many technical fields, has its own complex terminology. Our courses break down these concepts into manageable units, avoiding unnecessary jargon. We present critical ideas in simple language, often using visual aids like images, tables, and lists to reinforce learning. Through smaller, digestible challenges, students are not overwhelmed, and they can build confidence by working on bite-sized tasks instead of one large, daunting project.
Encouraging Customizating Through Modularity
Codio’s Cybersecurity content isn’t a rigid, one-size-fits-all solution. The curriculum is structured in a modular format, with natural break points where instructors can adapt the material to best suit their teaching objectives. Whether reordering topics, renaming units, or adding custom content, instructors can easily tailor the learning experience. Codio’s flexible authoring tools also allow instructors to create their own content, ensuring that the course meets the specific needs of their students while maintaining a strong focus on cybersecurity fundamentals.